* Build with kubernetes 1.24 libraries * Try to resolve circle build error * Fix build warnings * Update test parser to use modern command install method * Attempt to pass helm chart testing * Correct testing kube version * Update go version used by the drone ci * Remove beta versions from templetes |
||
|---|---|---|
| .circleci | ||
| .dependabot | ||
| .pipeline | ||
| .scripts | ||
| .test | ||
| approvals | ||
| bot | ||
| chart/keel | ||
| cmd/keel | ||
| constants | ||
| deployment | ||
| extension | ||
| internal | ||
| pkg | ||
| provider | ||
| registry | ||
| secrets | ||
| static | ||
| tests | ||
| trigger | ||
| types | ||
| ui | ||
| util | ||
| version | ||
| .drone.yml | ||
| .gitignore | ||
| Dockerfile | ||
| Dockerfile.aarch64 | ||
| Dockerfile.armhf | ||
| Dockerfile.debian | ||
| Dockerfile.local | ||
| LICENSE | ||
| Makefile | ||
| go.mod | ||
| go.sum | ||
| readme.md | ||
readme.md
Keel - automated Kubernetes deployments for the rest of us
- Website https://keel.sh
- Slack - kubernetes.slack.com look for channel #keel
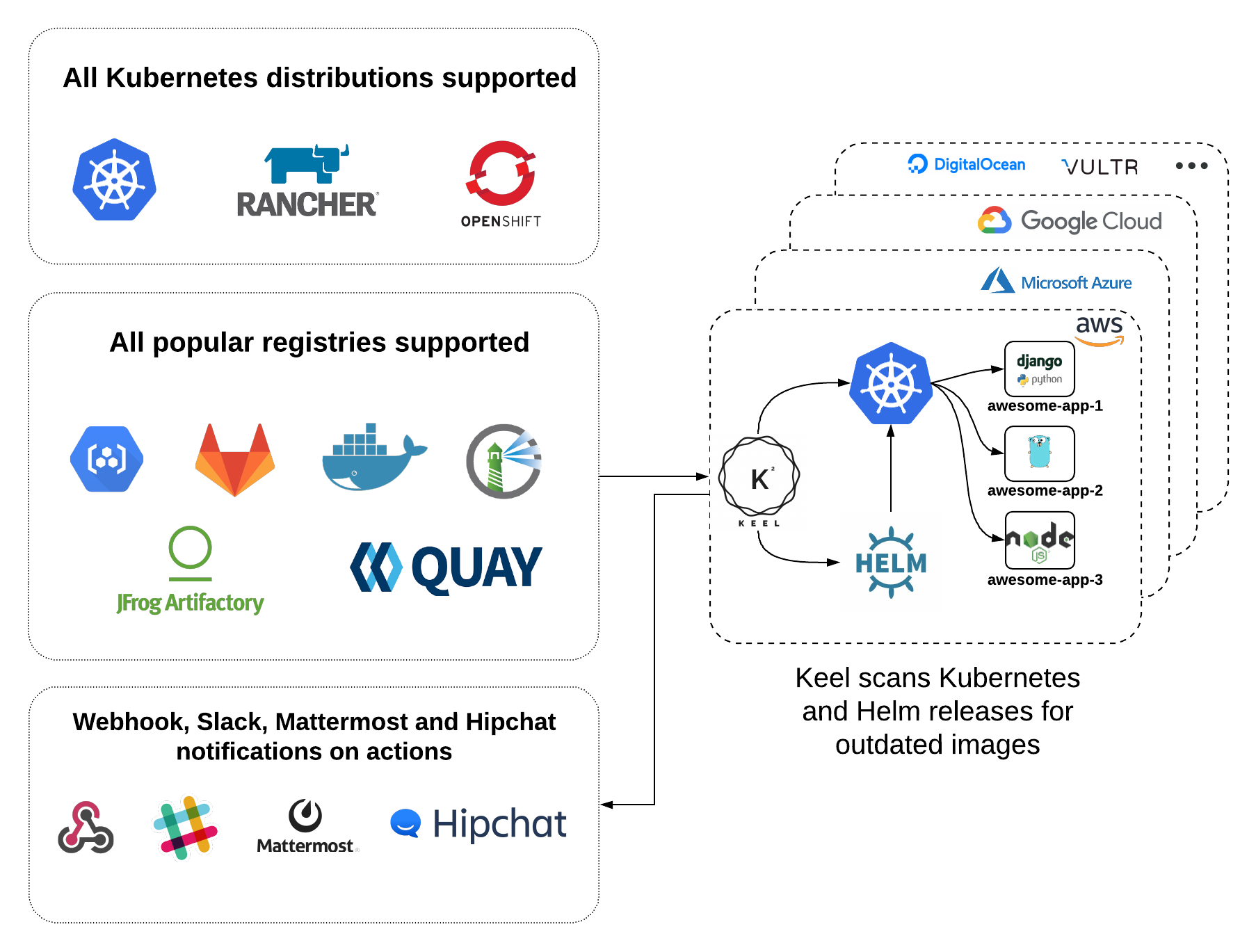
Keel is a tool for automating Kubernetes deployment updates. Keel is stateless, robust and lightweight.
Keel provides several key features:
-
Kubernetes and Helm providers - Keel has direct integrations with Kubernetes and Helm.
-
No CLI/API - tired of
f***ctlfor everything? Keel doesn't have one. Gets job done through labels, annotations, charts. -
Semver policies - specify update policy for each deployment/Helm release individually.
-
Automatic Google Container Registry configuration - Keel automatically sets up topic and subscriptions for your deployment images by periodically scanning your environment.
-
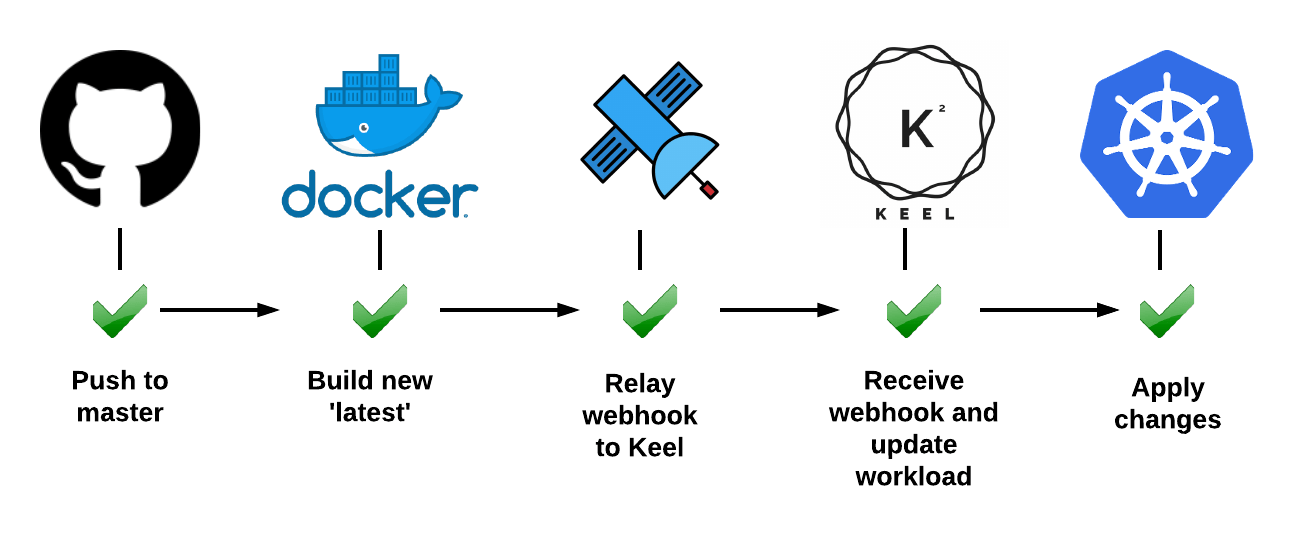
Native, DockerHub, Quay and Azure container registry webhooks support - once webhook is received impacted deployments will be identified and updated.
-
Polling - when webhooks and pubsub aren't available - Keel can still be useful by checking Docker Registry for new tags (if current tag is semver) or same tag SHA digest change (ie:
latest). -
Notifications - out of the box Keel has Slack, Hipchat, Mattermost and standard webhook notifications, more info here
Support
Support Keel's development by:
- Patreon
- Paypal
- Star this repository
- Follow on Twitter
Warp speed quick start
To achieve warp speed, we will be using sunstone.dev service and Minikube.
Start Minikube:
minikube start
Install customized Keel (feel free to change credentials, namespace and version tag) straight from your kubectl.
# To override default latest semver tag, add &tag=x.x.x query argument to the URL below
kubectl apply -f https://sunstone.dev/keel?namespace=default&username=admin&password=admin&tag=latest
# and get Keel IP:
minikube service --namespace default keel --url
http://192.168.99.100:3199
We are overriding default latest semver tag with latest since it has the new UI. If you want to use latest semver, just remove the
&tag=latestpart from the URL.
Creating remotely accessible Keel instance
Keel can work together with webhook relay tunnels. To deploy Keel with Webhook Relay sidecar you will need to get a token, then pre-create a tunnel and:
kubectl apply -f https://sunstone.dev/keel?namespace=default&username=admin&password=admin&relay_key=TOKEN_KEY&relay_secret=TOKEN_SECRET&relay_tunnel=TUNNEL_NAME&tag=latest
Now, you can access Keel remotely.
Helm quick start
Prerequisites:
- Helm
- Kubernetes
You need to add this Chart repo to Helm:
helm repo add keel https://charts.keel.sh
helm repo update
Install through Helm (with Helm provider enabled by default):
helm upgrade --install keel --namespace=kube-system keel/keel
If you work mostly with regular Kubernetes manifests, you can install Keel without Helm provider support:
helm upgrade --install keel --namespace=keel keel/keel --set helmProvider.enabled="false"
To install for Helm v3, set helmProvider.version="v3" (default is "v2"):
helm install keel keel/keel --set helmProvider.version="v3"
That's it, see Configuration section now.
Quick Start
A step-by-step guide to install Keel on your Kubernetes cluster is viewable on the Keel website:
https://keel.sh/examples/#example-1-push-to-deploy
Configuration
Once Keel is deployed, you only need to specify update policy on your deployment file or Helm chart:
apiVersion: extensions/v1beta1
kind: Deployment
metadata:
name: wd
namespace: default
labels:
name: "wd"
annotations:
keel.sh/policy: minor # <-- policy name according to https://semver.org/
keel.sh/trigger: poll # <-- actively query registry, otherwise defaults to webhooks
spec:
template:
metadata:
name: wd
labels:
app: wd
spec:
containers:
- image: karolisr/webhook-demo:0.0.8
imagePullPolicy: Always
name: wd
command: ["/bin/webhook-demo"]
ports:
- containerPort: 8090
No additional configuration is required. Enabling continuous delivery for your workloads has never been this easy!
Documentation
Documentation is viewable on the Keel Website:
https://keel.sh/docs/#introduction
Contributing
Before starting to work on some big or medium features - raise an issue here so we can coordinate our efforts.
We use pull requests, so:
- Fork this repository
- Create a branch on your local copy with a sensible name
- Push to your fork and open a pull request
Developing Keel
If you wish to work on Keel itself, you will need Go 1.12+ installed. Make sure you put Keel into correct Gopath and go build (dependency management is done through dep).
To test Keel while developing:
- Launch a Kubernetes cluster like Minikube or Docker for Mac with Kubernetes.
- Change config to use it:
kubectl config use-context docker-for-desktop - Build Keel from
cmd/keeldirectory. - Start Keel with:
keel --no-incluster. This will use Kubeconfig from your home.
Running unit tests
Get a test parser (makes output nice):
go get github.com/mfridman/tparse
To run unit tests:
make test
Running e2e tests
Prerequisites:
- configured kubectl + kubeconfig
- a running cluster (test suite will create testing namespaces and delete them after tests)
- Go environment (will compile Keel before running)
Once prerequisites are ready:
make e2e